In many competitions, getting a 9.8 of 10 would be considered a great accomplishment. What you do not want to score highly on is a CVSSv3 base score, and that is what VMware is at with this one. For VMware vCenter server there is a new CVE (CVE-2021-22005) that is quite scary making it a very easy to execute attack vector that offers great access to systems. An unauthenticated user, if they can access port 443, can upload a file and run commands on a VMware vCenter server. What is more, this has implications for VMware Cloud Foundation, and solutions such as Dell EMC’s VxRail and HPE SimpliVity.
VMware vCenter VMSA-2021-0020 and CVE-2021-22005
First off, let us discuss the scope of impact. This vulnerability impacts VMware vCenter Server 6.5, 6.7, and 7.0 (save perhaps vCenter Server 7.0 Update 2c Build 18356314 and 6.7 Update 3o Build 18485166) as supported products. If you are running a recent VMware version, you most likely need to patch it immediately. VMware suggests given the scope and ease of exploitation that this is treated with an emergency change.
While VMSA-2021-0020, as the security advisory, discusses several vulnerabilities, CVE-2021-22005, is perhaps the most important. Per VMware this is:
“[A] file upload vulnerability that can be used to execute commands and software on the vCenter Server Appliance. This vulnerability can be used by anyone who can reach vCenter Server over the network to gain access, regardless of the configuration settings of vCenter Server.” (Source: VMware)
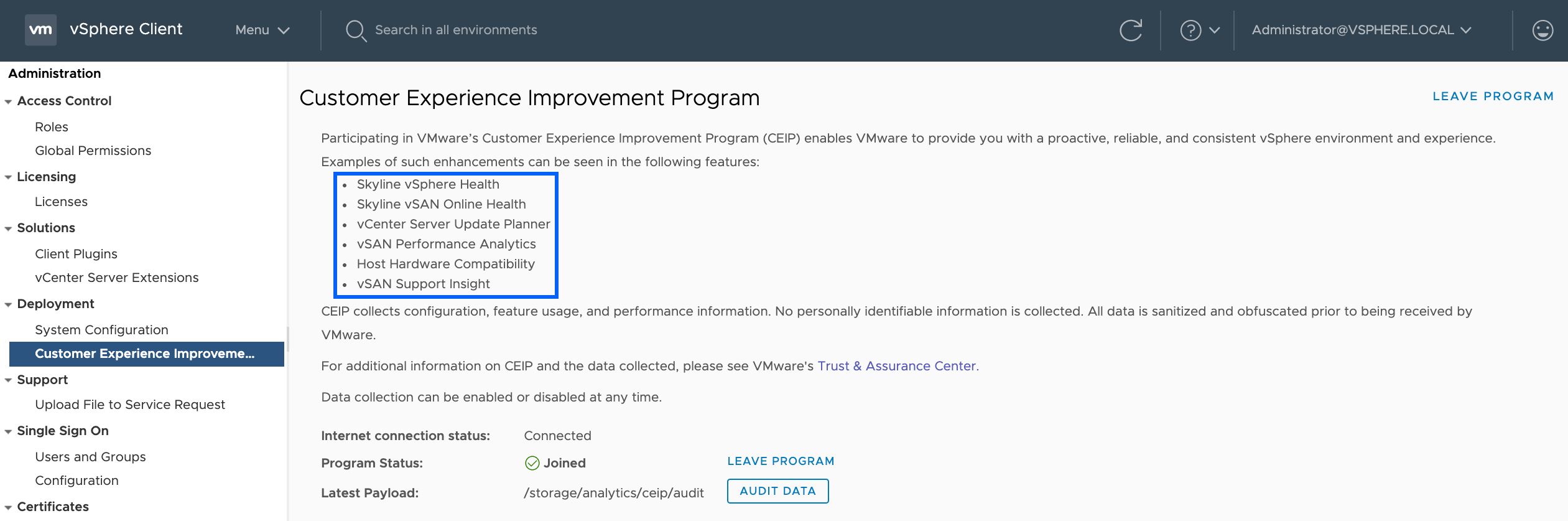
What is more, the VMware Customer Experience Improvement Program (CEIP) Analytics service that is the target of the vulnerability is still vulnerable even if it is not used and one disables it via the VMware vCenter GUI.
Engineered Solutions Have Another Challenge
In the VMware FAQ about this change, the company specifically called out Dell EMC VxRail, HPE SimpliVity, and VMware’s own Cloud Foundation. These are engineered solutions that control patch levels as part of their qualification processes. As such, those systems need to be patched for these vulnerabilities in line with the overall solution’s patch processes.
For example, we did not see a Dell EMC VxRail or HPE SimpliVity update CVE-2021-22005. If our readers see one of those, then feel free to drop them in the comments to help other STH readers.
Final Words
Remote code execution (RCE), by unauthenticated users, simply with access to a common port seems very scary. That is likely because it is. We normally do not post lower-scored vulnerabilities, even like the recent Netgear web interface vulnerability, but this one we want to make sure our readers are aware of. It is too big to leave unpatched.



Thank you STH for getting this out. If you’re a fellow STH reader, you’ve got to patch this. It’s real bad.
For VxRail vCenter 7.0 U2c is included with the 7.0.240 code, no word yet for 4.7.X. This would only apply if vCenter in internal/managed by VxRail otherwise, external vCenters can be upgraded outside of VxRail code