This release feels like a long time in the making. pfSense 2.4.0 was released on 12 October 2017 and 2.4.4-RELEASE-p3 arrived on 20 May 2019. That means we had a period of around ten months since the last release until today’s pfSense 2.4.5 release. For those keeping track, the original 2.4.4 release happened on 24 Sep 2018 or over a year and a half ago. With the new update, we can see some changes, but the bigger update will happen with the next version.
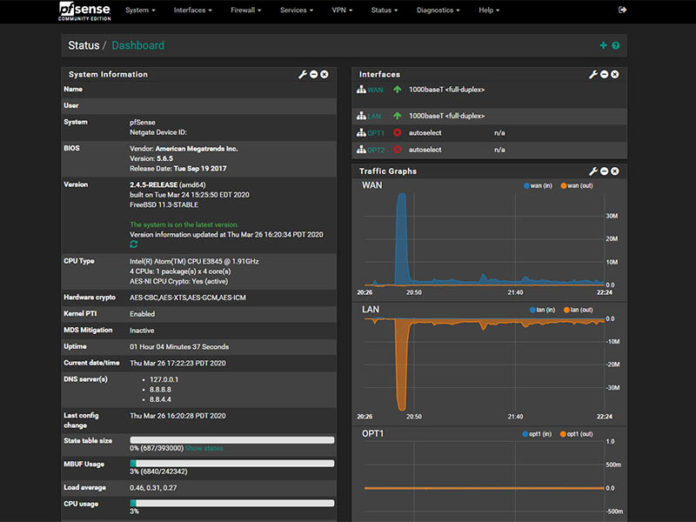
pfSense 2.4.5 New Features
There are several new features with the latest version:
- Base Operating System upgraded to FreeBSD 11-STABLE after FreeBSD 11.3
- Added sorting and search/filtering to several pages including the Certificate Manager, DHCP Leases, and ARP/NDP Tables.
- Added DNS Resolver (Unbound) Python Integration
- Added IPsec DH and PFS groups 25, 26, 27, and 31
- Changed UFS filesystem defaults to
noatimeon new installations to reduce unnecessary disk writes - Set
autocomplete=new-passwordfor forms containing authentication fields to help prevent browser auto-fill from completing irrelevant fields - Added new Dynamic DNS providers Linode and Gandi
For a complete list of new features, see the Release Notes. (Source: Netgate/ pfSense)
For most, these are going to be mostly back-end changes but moving to FreeBSD 11.3 also means we get updated drivers which are always appreciated for those using newer hardware. There are also a host of security and bug fixes that made it into this release which you can read about in the release notes.
One piece of advice the pfSense team gave was to not update/ upgrade remote systems if you cannot get to them. That goes for not just pfSense but all hardware as we start to see even colocation providers close their doors to customer visits.
Looking Ahead
Looking ahead, something many of our users need to be aware of is that there is a big change coming for pfSense 2.5.0. With the next version, we will finally see the depreciation of the built-in pfSense load balancer relayd since it will not work with the newer OpenSSL versions. As a result, the pfSense ecosystem is going to effectively be migrated to using HAproxy for load balancing and reverse proxy duties. Moving load balancing to a package will have the impact of changing how the pfSense features are bundled and will require users to make a change if they are using the built-in load balancer. At STH, we were using pfSense and the HAProxy HA/ load balancer in 2015.
Another big change coming is that we will see an update to FreeBSD 12 with the new pfSense 2.5.0. That is causing some of these changes but should again bring better hardware support. On the subject of hardware, pfSense will not require AES-NI with 2.5.0 as originally planned. For some low-end appliance users, this is great news, but at the same time, we recommend to all STH readers to only buy new hardware with crypto acceleration. The time has come where this should be a must-have feature.
If you see any pfSense 2.4.5 or 2.5.0 feature changes that jump out at you, feel free to call them out in the comments.



When are they pushing to the newly re-written python3 based stack with the integrated API?
is that still on the table for pfsense 3.0+ ?
YES! Nice fix here with the update; my gateway group containing two OpenVPN interfaces now splits the traffic evenly. Thanks for pointing out the update availability.
this means nothing, until they don’t implement an api based configuration alt least for the basic services like DNS, DHCP, TCP/IP
AES-NI should not become mandatory. I have a 12-years old computer which runs pfSense good enough for me. I do not wish to remain without updates.
Besides old hardware, AES-NI passthrough still does not work properly in Proxmox.
Addendum: actually, I failed to notice before, but hardware crypto is showing up in pfSense on Proxmox now. This must be pretty recent, like as of 6.1 or even a subrevision of. I don’t even see it mentioned in release notes. And I was wondering why CPU load was so low when there are literally 5x more VPN logins
than was intended.
This is about time.
Something as important as a firewall that is publicly connected should get regular security fixes.
Can’t belive it has been a year since the last update.
Just an FYI for everyone, that opnsense a fork of pfsense has already got an API , better looking interface and regular updates. So I highly recommend people check it out at opnsense.org and not to mention in a few months will be releasing 20.7 that is based on hardenedBSD 12