Jintide bills itself as a security-enhanced Intel Xeon server CPU. Realistically, it is an auditing mechanism for Intel CPUs. The motivations are fairly clear, it is to build a harness that can intercept memory and I/O from a Xeon CPU and check to ensure that the chip and platform are presenting what one would expect. If that seems dense, let us go into the presentation, at Hot Chips 31, and delve into why.
Jintide Security Auditing Platform for Intel Xeon CPUs
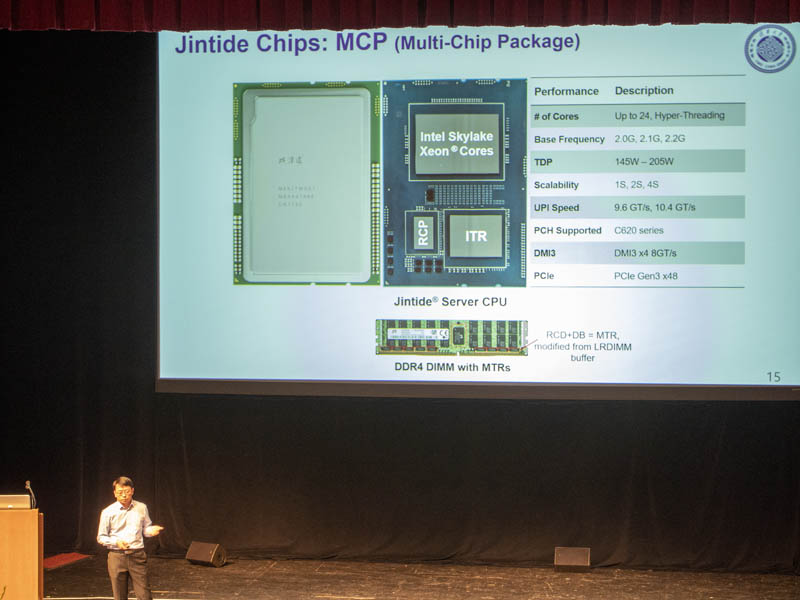
The Jintide solution has a few main components. At the center is a custom package that combines an Intel Skylake generation Xeon CPU with two Jintide chips. We are going to get to those shortly. Beyond the main package, custom DIMMs must also be used in the platform. Jintide showed this off specifically in a Lenovo platform. The motivation is clear, accelerate the discovery of vulnerabilities that can be introduced into a complex chip.
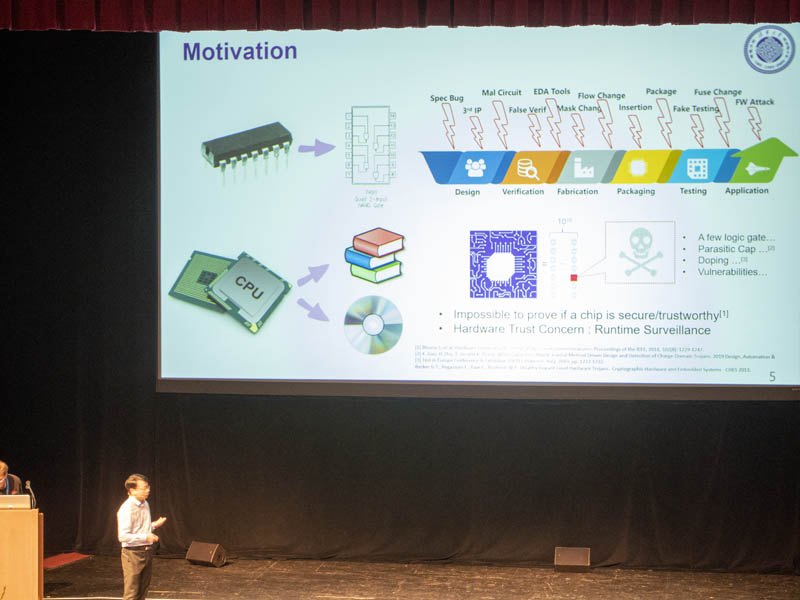
There are so many variables in modern servers and the chips are so complex, an auditing tool that can test for vulnerabilities is needed.
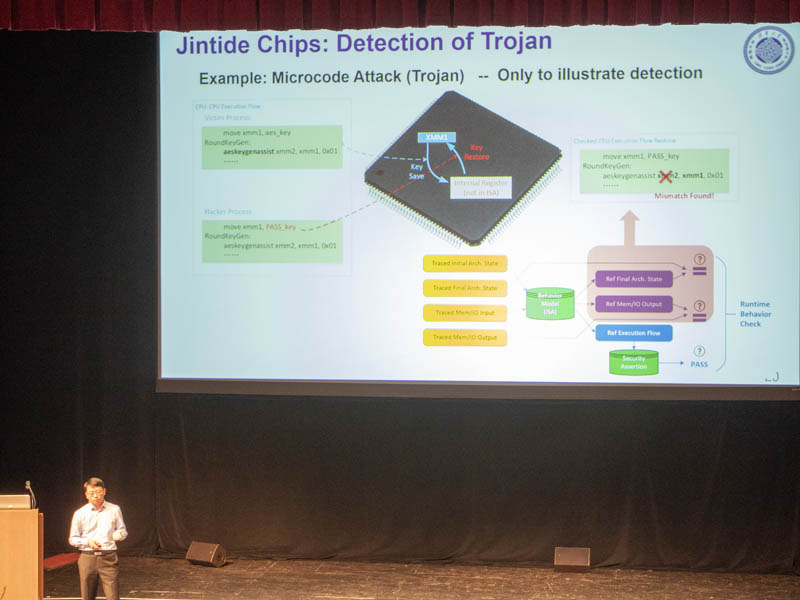
Two examples are finding Spectre/ Meltdown, L1TF, and other vulnerabilities. It can also be used to detect latent trojan logic in a system that changes behavior over what is expected.
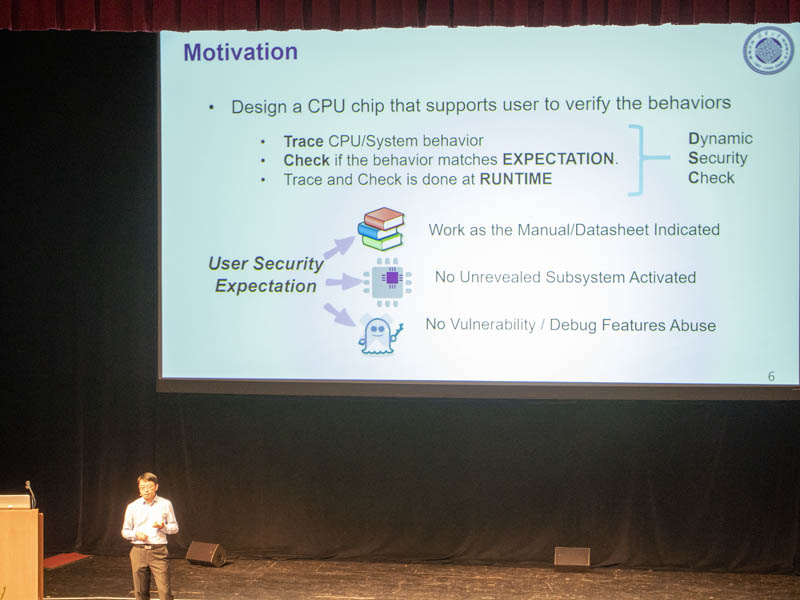
With that problem, Jintide, with Intel’s help, created an auditing solution.

We are going to get to the solution next.
Jintide Security Auditing Platform for Intel Xeon CPUs
The overall solution includes both a custom CPU package as well as custom DDR4 modules.
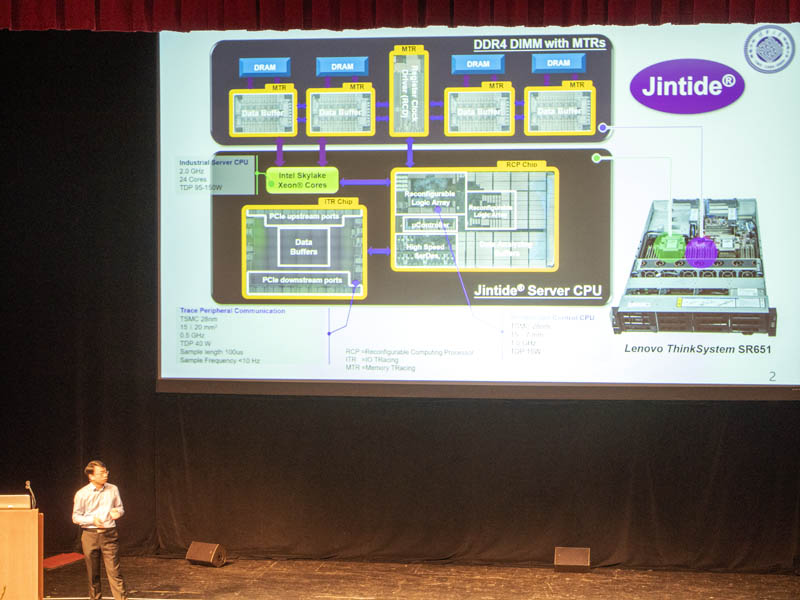
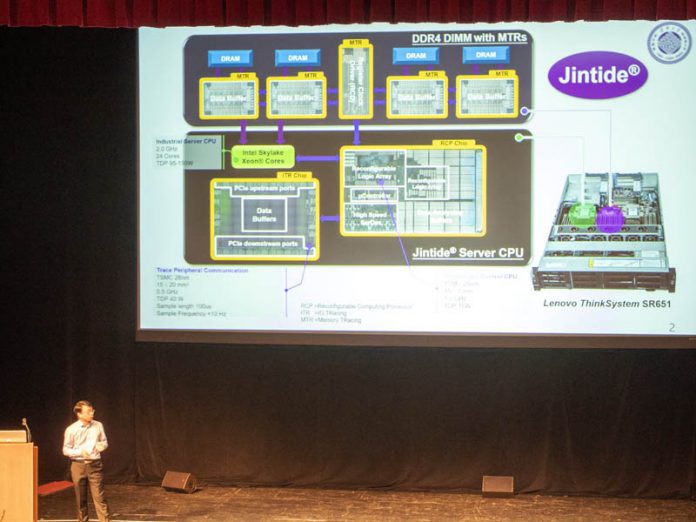
Here is a diagram of the solution, but the short answer is that the solution is designed to monitor all memory and I/O messages to a CPU. That way, one can sample what a CPU is doing and potentially detect vulnerabilities or validate proper operation.
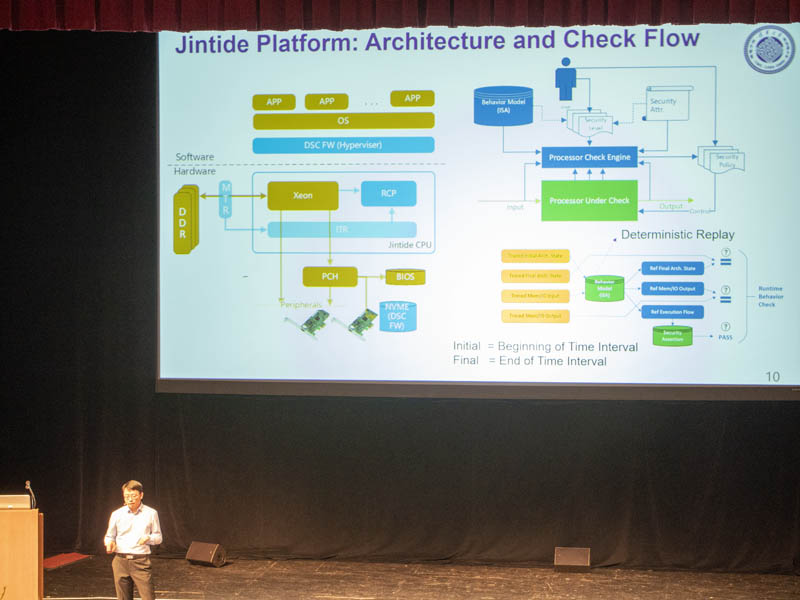
The DIMMs repace the register and buffer are replaced with the memory tracing registers. These allow Jintide to validate the flow of information from the CPU to memory. There are also two new chips added to the CPU package.
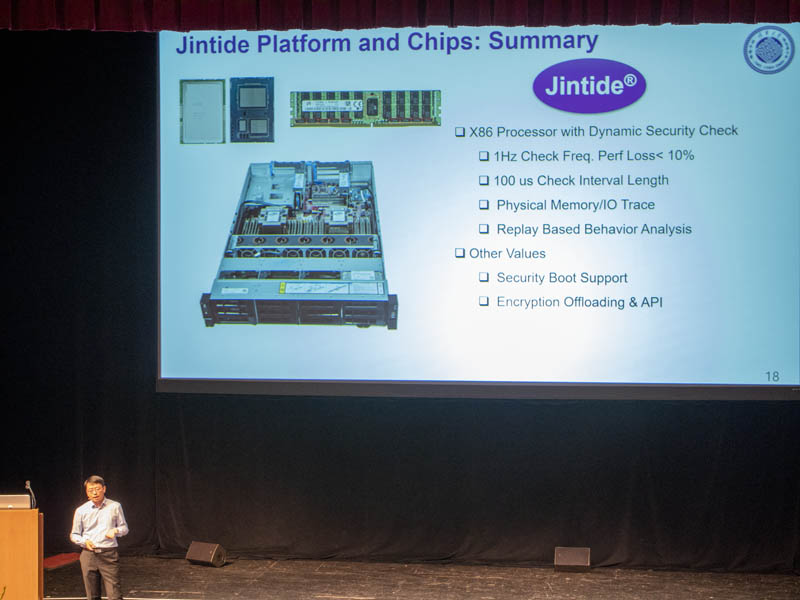
Here is a look at the solution. Due to the two new chips, it can only be configured with up to 24 cores. These can also be configured for multi-CPU scenarios. Due to the additional TDP from the Jintide chips still have up to a 205W TDP.
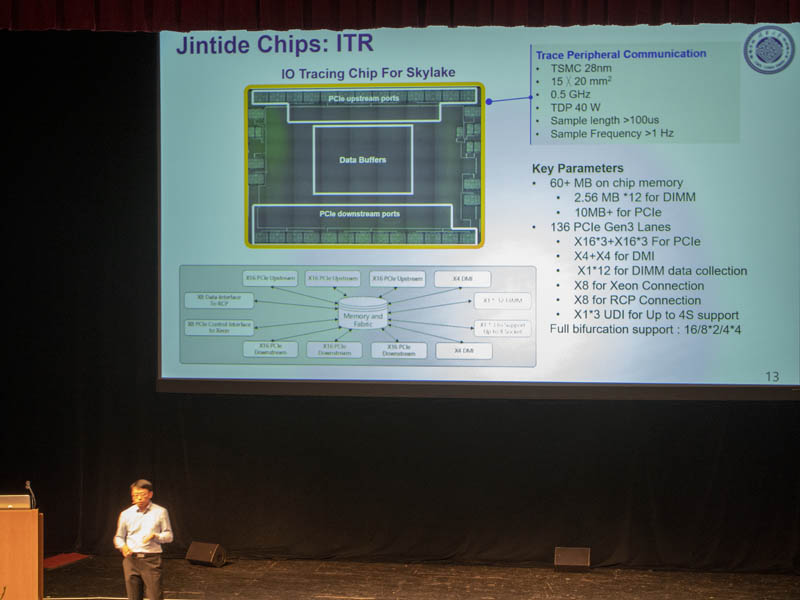
The Jintide ITR can monitor PCIe traffic and has data buffers to monitor the PCIe I/O of the system. Fabbed on TSMC 28nm, it has a 40W TDP and also has the memory to store all of the sampling data.
The smaller chip is the 15W TDP RCP chip has reconfigurable logic arrays to help analyze what the CPU is doing.
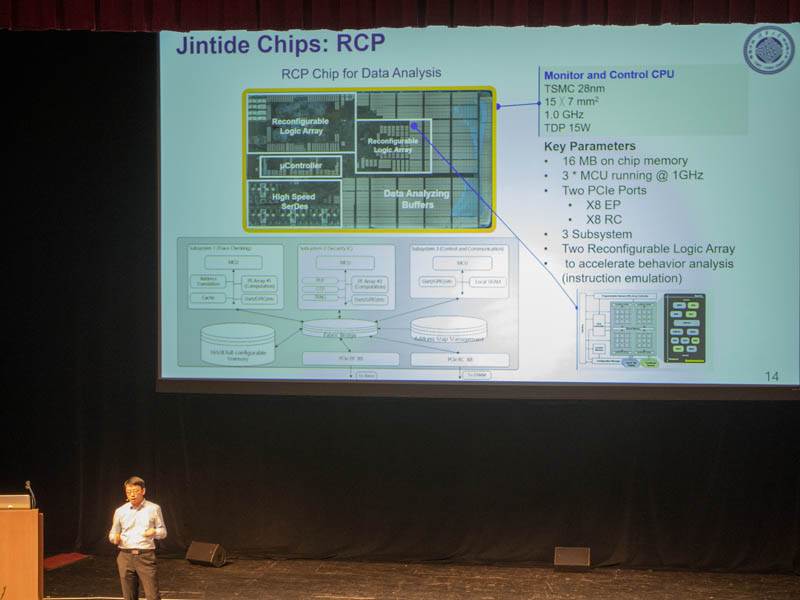
If you wanted to see everything a CPU is doing, this is a great test harness to do so. Adding 55W of validation chips and using lower volume packaging is not something we expect to make it to mainstream volume servers. It is possible these are used in certain sensitive applications and labs.
Final Words
There is performance loss by sampling, but one can select sampling frequency to either increase the chance of detection or increase performance. It is not hard to understand why this chip exists. In theory, it could be deployed, but realistically, this version looks more like an auditing tool. Adding additional logic that monitors all memory and I/O messages mean that the Jinade tool itself represents a potential vulnerability. As an auditing tool, this is not as big of a concern but it would be a major one in deployment.
The scope was limited to Skylake Xeons but at Hot Chips 31 no other designs were disclosed. One could see this as a valuable tool for Intel to test the impacts of security mitigations as it evolved its Skylake cores to the 2nd Gen Intel Xeon Scalable platform that had many security enhancements.




Adding chips to your platform that can directly sample CPU and RAM sounds like a brilliant way to introduce vulnerabilities and attack vectors. Maybe Intel forgot about their own IME disasters or simply concluded that if this solution doesn’t have Intel branding it won’t backfire as hard when eventually it turns out to be vulnerable.
I see this as an interesting forensics tool. It says something about Intels chips, that this even exists…