Google Cloud is making a splash in the confidential computing space. While Google Cloud encrypts data at-rest (e.g. in storage) and in-transit (over the network), there is more to be done. When data is brought from storage to the CPU and RAM to be processed, it is generally decrypted. Using AMD’s SEV (Secure Encrypted Virtualization) in EPYC processors, Google is able to keep data encrypted even in memory.
AMD EPYC 7002 Secure Encrypted Virtualization
The AMD EPYC 7002 “Rome” chips had a big boost around memory encryption. One of the prime examples is that, compared with the EPYC 7001 “Naples” products, we got a large expansion in the number of memory keys the chips could handle. This is that kind of change we typically see when a large customer likes a concept, but finds a limitation that they need to be removed in order to make the chips generally deployable.
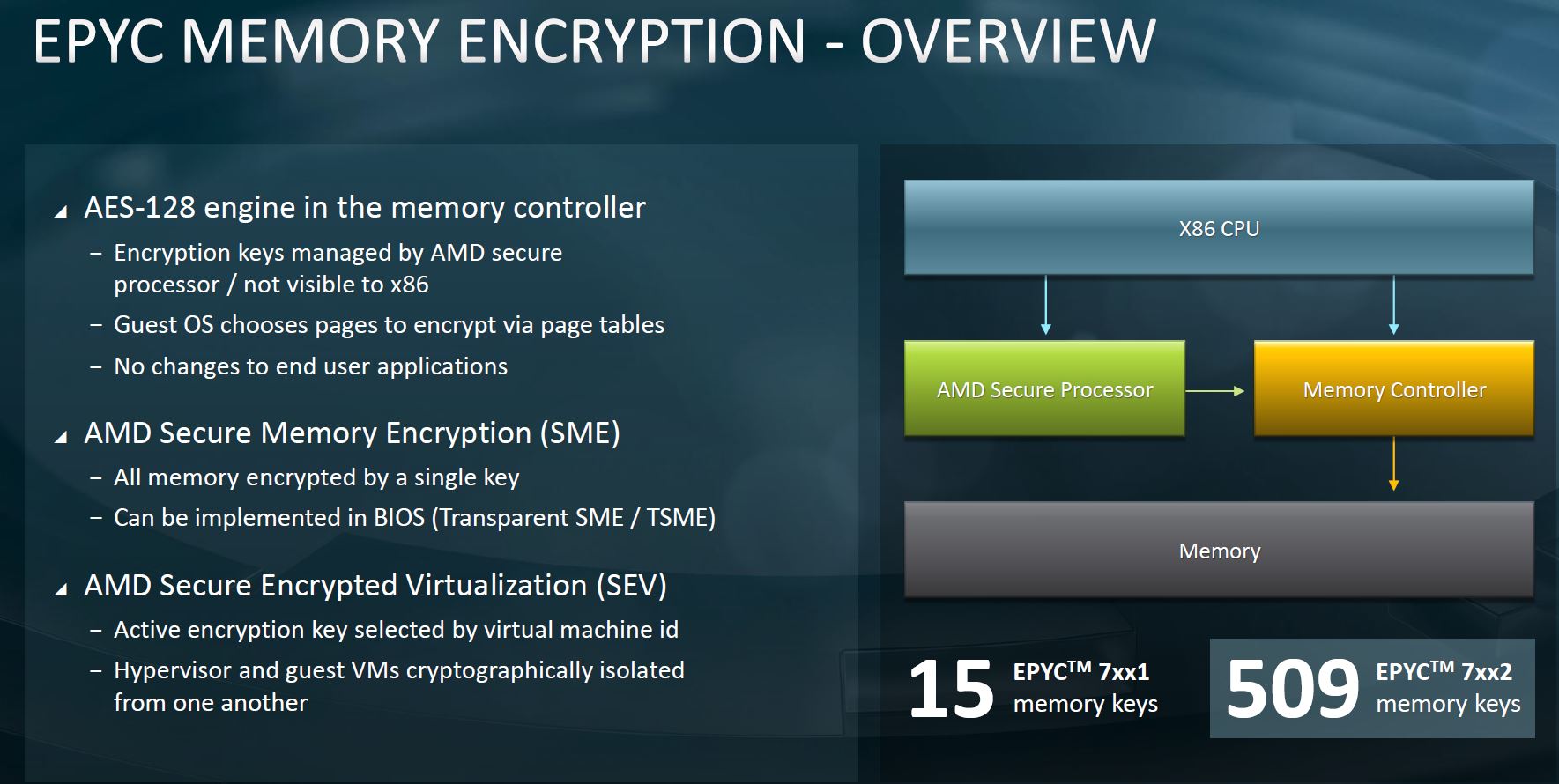
While at STH, we use SME even in our hosting cluster, Google Cloud is using SEV which makes a lot of sense in a cloud infrastructure.

The key impact is that this keeps the VMs and data they are storing in memory encrypted to protect the workloads from other tenants and even the infrastructure operator. This is the key technology Google is using.
Google Cloud Confidential VMs
One of the biggest developments for Google Cloud confidential VMs was making the process easy. One can effectively check a “Enable Confidential Computing service on this VM instance” checkbox and the service will run. There are pre-requisites because the VM will need to be scheduled on an AMD machine, but this is fairly easy to get a next-level of encryption.

Google also shared an example showing that AMD Secure Encrypted Virtualization (SEV) is active.
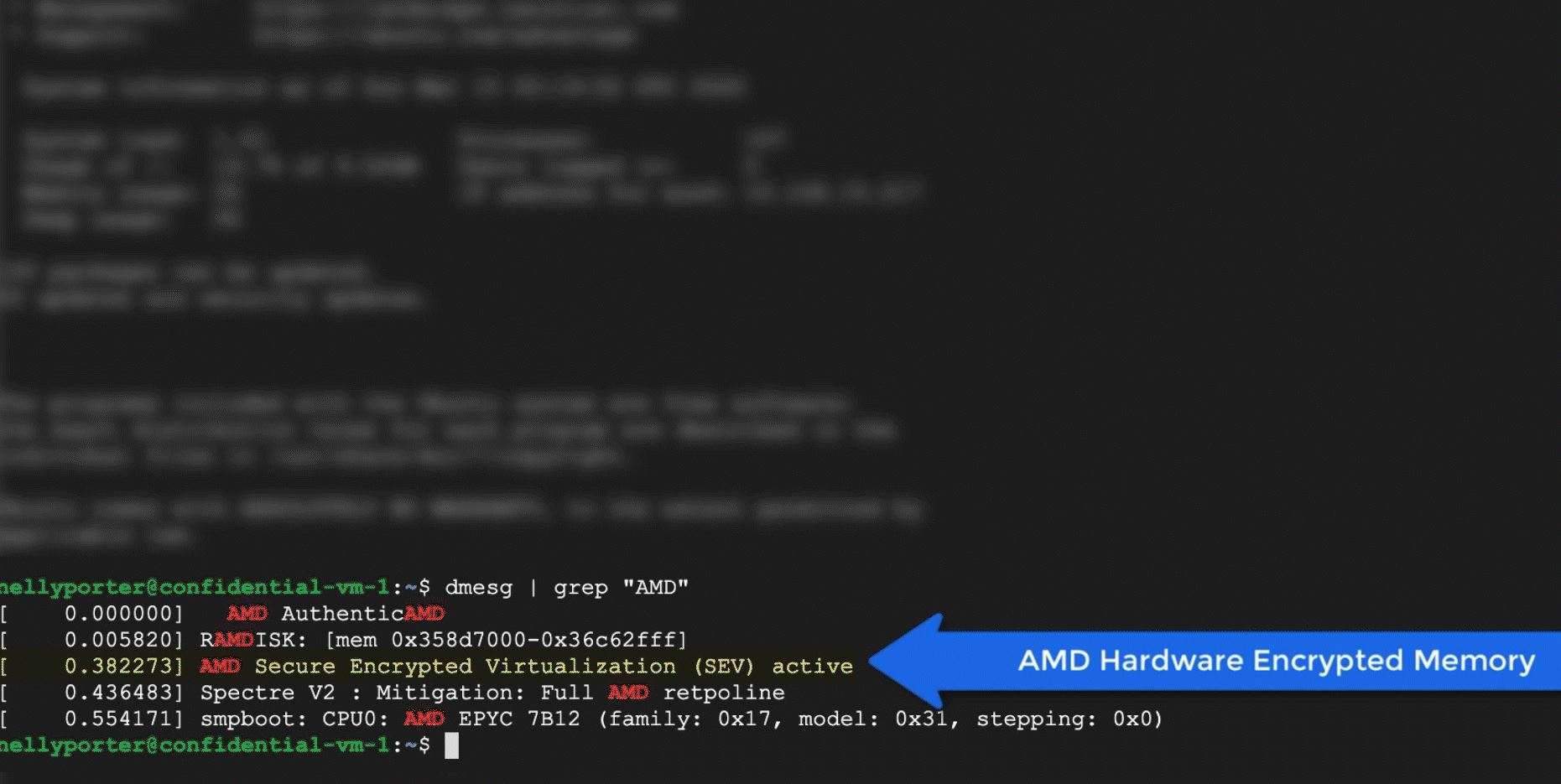
Although Google is using an AMD EPYC 7B12 that you cannot purchase, the SEV feature is available on AMD EPYC 7002 series “Rome” parts.
As you can see that the command above is being issued by a “nellyporter”. It turns out that Nelly is the Google Cloud PM lead for Confidential VMs so I was able to ask a few questions about targeting as well as the roadmap.
Patrick Kennedy: What customer/ vertical/ applications does Google see as early and near-term adopters? What is driving that adoption?
Nelly Porter: Confidential VMs can help all our customers protect sensitive data, but we think it will be especially interesting to those in regulated industries such as financial services, healthcare, and the public sector. As we see more organizations move workloads to the cloud, one of the biggest concerns they have is how to process sensitive data while keeping it private, especially these customers in regulated industries. Confidential VMs help to remove some of these barriers to the cloud, so customers can take full advantage of the innovation the cloud has to offer.
PK: What is Google offering in terms of a roadmap for customers who do leverage Confidential VMs?
NP: With Confidential VMs, we’ve simplified the overall provisioning and workflow to use this technology, which is a key differentiator in the Confidential Computing space. By making it nothing more than a checkbox for customers to leverage, we hope Confidential VMs become mainstream for our users. The next step for us is to extend confidential computing to an even broader set of GCP services.
Final Words
Confidential computing is still in its early days. Looking beyond this announcement, we fully expect that this will become more commonplace in public clouds within the next 18-24 months. Beyond AMD’s “Rome” today and the next-gen EPYC 7003 “Milan” chips, we expect Intel to expand SGX functionality and memory encryption in Ice Lake Xeons as they round out the 3rd gen Intel Xeon Scalable lines. There are also non-x86 vendors working in this space. As we see the hardware proliferate to make this possible, we expect confidential computing to be more commonplace. It is great to see Google forging ahead early in the capability lifecycle here.



Informative as usual… I’m interested to see the adoption of the 4p/8P that AMD defined by saying Milan supports 100% of the TAM… SEV and SME already enabled a much better base station platform with the 3xxx series and now I expect a more performant HPC level APU