Gigabyte has released their new Intel Xeon E5 series server motherboards recently. As most server vendors do, Gigabyte has a IPMI 2.0 interface for the new LGA 2011 motherboards. After looking at both the Supermicro IPMI web management interface and the Tyan IPMI web GUI, I wanted to give a quick tour of the Gigabyte IPMI 2.0 web management implementation. Gigabyte uses a different web management solution versus what one gets from Supermicro, Intel and Tyan. Those three typically use the MegaRAC interface and then add customizations on top of that. Gigabyte went with the Avocent MergePoint solution which Dell also uses on PowerEdge servers. I am breaking this into two parts because there is a lot here and some significant differences. The Gigabyte Server Motherboard IPMI Walkthrough – Part 2 covers the KVM-over-IP as well as the ability to remotely mount images and view sensors/ event logs.
The process for getting to Gigabyte’s server management interface is similar to that of other vendors. One first needs to locate the IPMI 2.0 network address. I used two easy methods, checking the pfsense firewall appliance as well as using Supermicro IPMIview 2. One is presented with a logon page. The default username and password were: admin // password
One can see the Gigabyte branding but also the Avocent MergePoint Embedded Management Software mark. Gigabyte has at least taken the opportunity to do some branding of the management interface which is a good practice.
Let’s look at the options once we are in. This piece will cover the configuration options while Part 2 will cover the diagnostic information and vKVM (KVM over IP) functionality, which is a key part for a systems administrator to use.
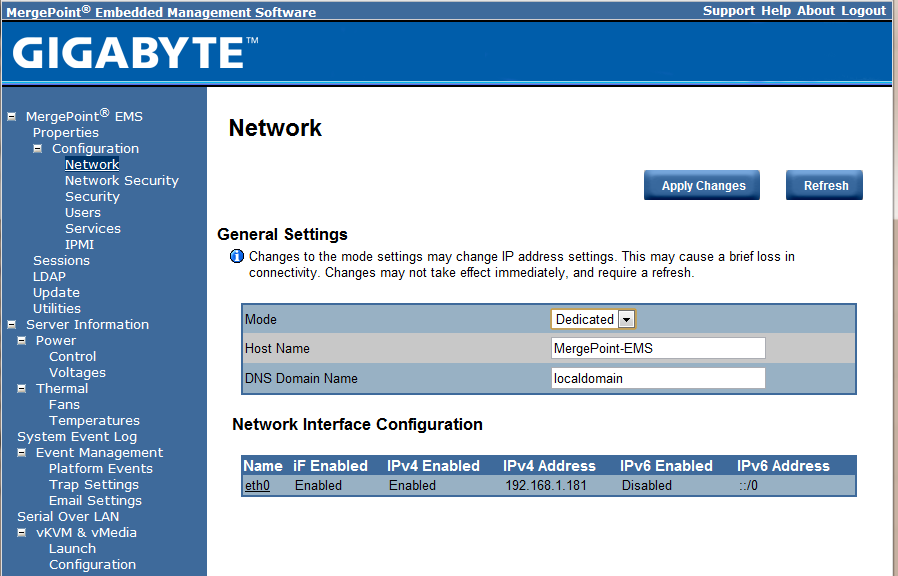
One can see that the Avocent web management engine allows for some customization on how one addresses the IPMI interface. From a security perspective, I like to ensure that all IPMI NICs are connected to a management network that I can VPN into. Depending on your setup, you may need either a static or dynamic IP address assigned. As an aside, I just plugged this into my office network to capture screenshots if anyone is wondering about the 192.168.1.* address.
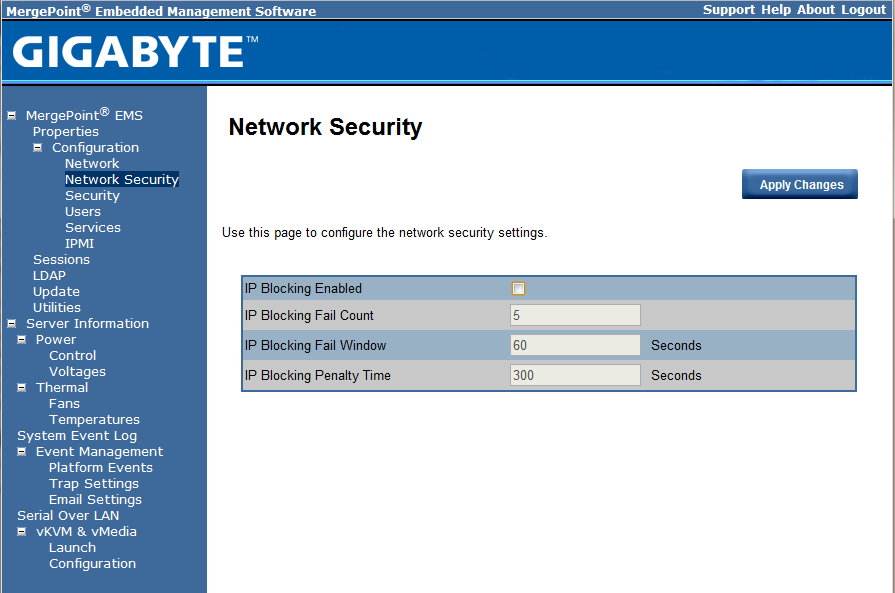
The Gigabyte’s solution allows one to do some basic network security on the IPMI management interface. Some solutions do not even offer this so it is good to see the Gigagbyte / Avocent solution addressing this in there server management interface.

Users
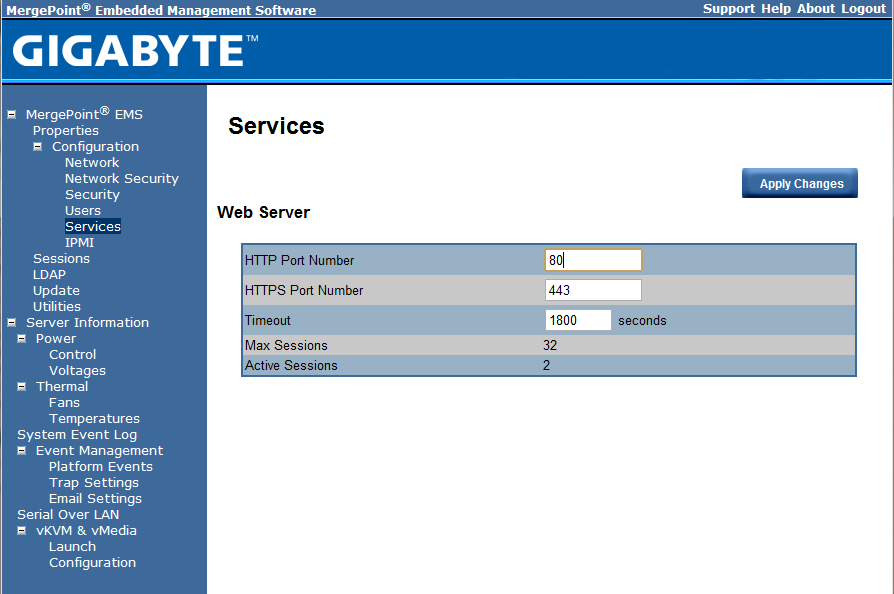
One can configure the web server settings for the Gigabyte IPMI web management. Many users will stick with default settings, but it is nice to have this control for those that do need to change these items.
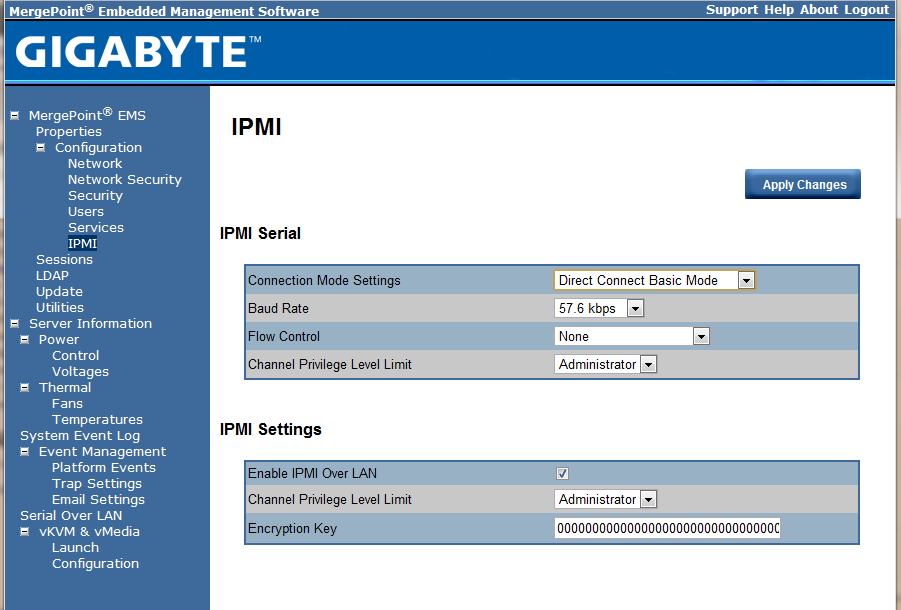
One can access the IPMI functions both over the management LAN (most common these days) and through serial connections. The Gigabyte solution provides the ability to enable or disable these server management pathways.
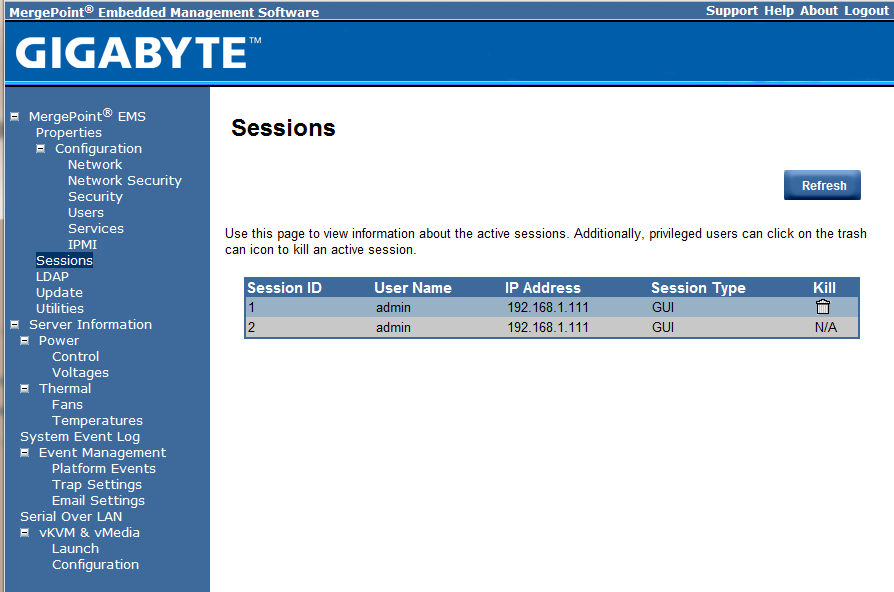
One can see the users that are logged into the management session. In this example I opened a session from Google Chrome and Microsoft Internet Explorer and saw two sessions active.
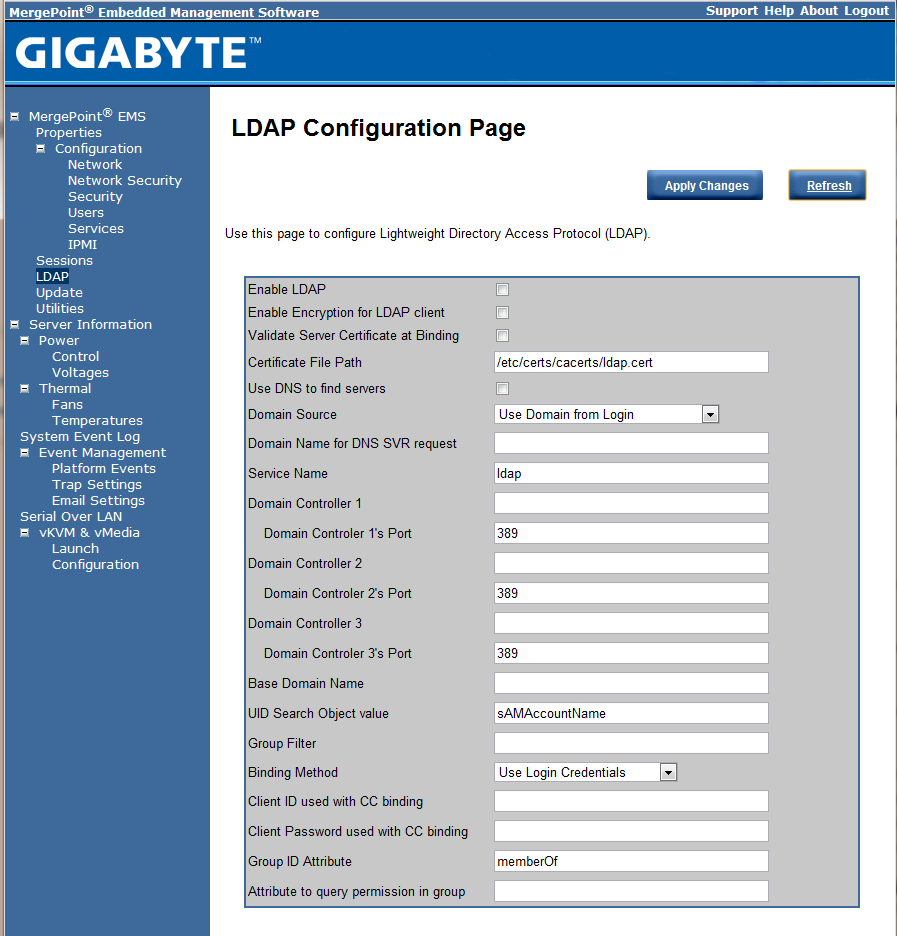
The Gigabyte management IPMI interface does include LDAP settings. For those that commonly use older server management platforms, this was not a common feature on IPMI implementations a few years ago. Today, most vendors include this.
That concludes the first part of the Avocent based IPMI management interface on the Gigabyte Intel Xeon E5 series motherboards. It is refreshing to see that Gigabyte chose a solid interface and IT administrators building servers alongside typical Dell PowerEdge configurations will certainly see some similarities. Stay tuned for the next version of this. I may also refresh the older guides in the coming weeks as the newer generation Intel Xeon E5 motherboards have some updates to the MegaRAC based server management tools. I expect to see a lot of the updates in the Ivy Bridge based Intel Xeon E3 based motherboards due after the Ivy Bridge Xeon launch.

Got a model number and link for this new board?
Review this week :-)
Just wondering if you still plan on working on Part 2. I am very curious to see how the vKVM and diagnostic info stack up against existing MegaRAC solutions used by both Tyan and Supermicro.
Paul, hold on for less than 24 more hours. Just need to finish putting words around the screenshots at this point.