We have a server bypass adapter in the lab. At the same time, we realized that it is a topic we have never covered on STH. As a result, we thought it would be worthwhile to introduce a server bypass network adapter and explain what it is used for before we get to the review.
What is a Server Bypass Adapter?
Server bypass adapters are network controllers, with a twist. They can usually be configured to allow traffic to either be blocked going from port to port or continue to pass in the event that power is cut.
Here is a simple example of where one might be used. One may want to look at all traffic flows either coming into a router or just after it. The obvious choice would be to put a box with one port going to the WAN side and the other going to the LAN side.
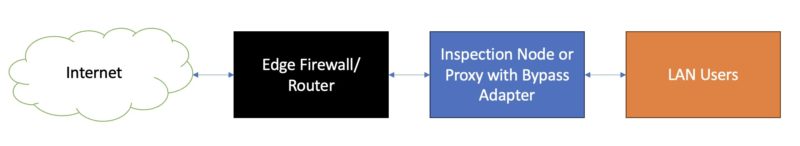
That box often does things like inspect flows for a firewall, but can also be used for applications like proxies.
The big challenge, of course, is what happens when that box needs to be restarted, or what if a power failure happens? If that machine is inline, then there needs to be a way to keep the connection online. One technique is to use a bypass adapter that effectively allows traffic to pass even when the machine is not online.
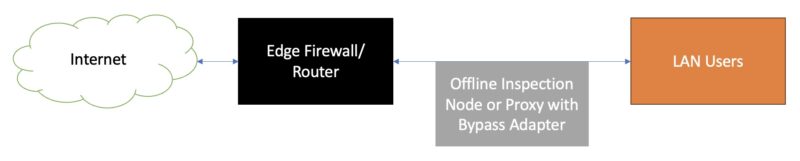
The above is perhaps an illustration of where a server bypass adapter is used. With a normal server adapter, when power fails, traffic between the ingress and egress ports stops. With a bypass adapter, the connection can be set to either closed or to continue passing traffic from port to port. In closed mode, traffic would stop. In bypass mode, traffic “bypasses” the node even if it is offline.
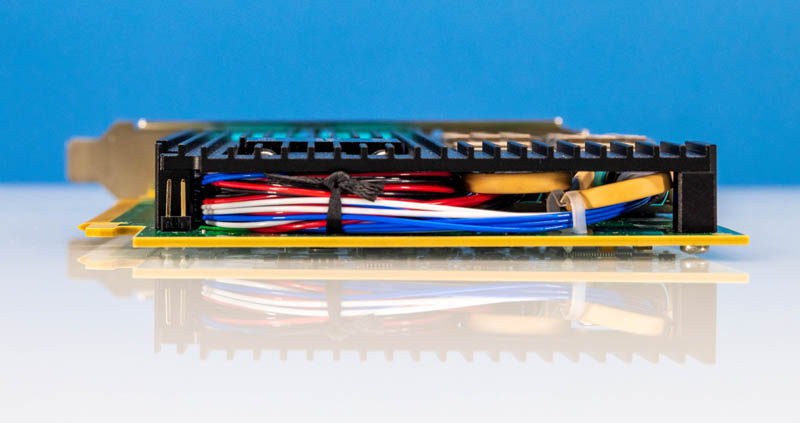
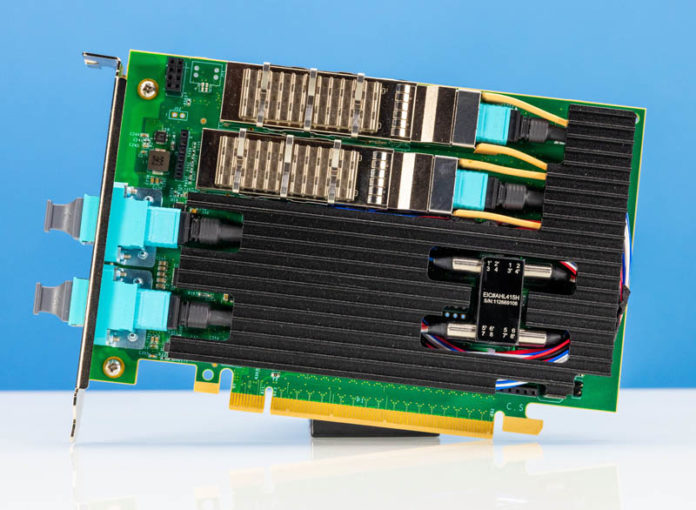
Here is an example of the Silicom 100GbE bypass network adapter we are going to look at on STH soon. This is much more complex than a standard network adapter and even the 1/10GbE copper versions. These bypass adapters have been around for generations, but the newer generations with fiber are more complex.
Final Words
Most of our readers, for most applications, will want standard network adapters. Still, we do have many readers looking to put together some high-end network topologies where things like a bypass network adapter can be used. There are other techniques that are used in networking to accomplish a similar task, but we wanted to at least have a quick guide. Hopefully, this helps our readers understand what a server bypass adapter is and where they are used.
Stay tuned for the Intel E810-based Silicom P4CG2BPi81 review coming soon on STH. If you have examples of where you have seen or used them, feel free to put them in the comments.




More than twenty years ago, I worked for a company that was selling an IDS solution that I believe used something like this to transparently inspect traffic.
From what I remember, at the time they had hacked together their own solution somehow with custom NIC and on top of that was running NFR and other tools to analyze the traffic at line rate.
We used these in a proxy app with a few thousand nodes behind them. It saved us like $15k per month
It definitely looks more complex than a regular fiber NIC. I’d love it if someone who knows more about these could explain what the extra bits do specifically, either a block diagram or a labeled picture
Looks like this card is more optical than electronic. I bet its got prisms in that H shaped piece.
I remember a 100 Mbit copper card that did something similar with relays, so when the card was unpowered it would click over into passthrough mode, and only moved into “interception” mode when the software turned on the relays.
You could achieve similar results by configuring a switchport in monitor-mode so it replays all frames sent from/to the firewall’s LAN side, but that doesn’t let the IDS host/proxy prevent the traffic.
I’ve never heard of those, are they mostly used for IDS / Packet Inspection? The language in title seems a bit tortured – is this intentional so it’s picked up by Google?
NEVER seen or heard of one of these, definitely would appreciate a deeper dive and maybe an accompanying vid. neat
these are pretty common in telcos for Deep Packet Inspection, PCEF and Proxy deployments
they basically are fail-open NICs that allow traffic to follow through if the system is off, or the NIC has been administratively “opened” (for patches etc)
you need this because to send traffic to a DPI, the router directs traffic over an interface and since the device doesn’t speak routing protocols, the router may not detect when it is down, hence fail-open (i.e. allow traffic to flow during maintenance or an outage preventing poor customer experience)
Lost me @ IDS
Load balancing.
High availability.
We’ve heard of them.
Any reason to use one of these over a passive fiber tap? Seems to me like a tap is more versatile and less complicated.
This is only a more complex form of TAPs – whether copper or optical that have been around for at least 20 years.
Any chance for an in-depth look at data diodes?
Certainly in a similar vein, and increasing popular for SCIFs and cyber recovery vaults.
Are there other air-gap or physical network control solutions?