This week, QNAP has a new ransomware malware threat called DeadBolt. In the announcement, there is a familiar twist: the mitigations are well-known. Indeed, this latest malware attack would be mitigated by simply following an article on STH or elsewhere.
QNAP Ransomware DeadBolt Targets Those Disregarding Security
A few weeks ago we discussed how you should Secure Your QNAP NAS Immediately From the Latest Wave of Attacks. QNAP has a feature that we believe should be installed and used as part of the initial setup called Security Counselor.
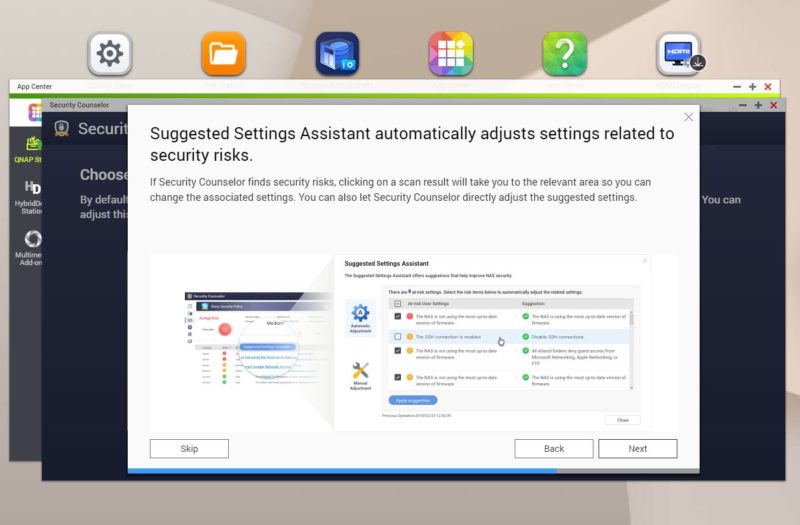
That actually has a check to detect if the NAS can be accessed directly from the Internet both on the administration service and web server sides.
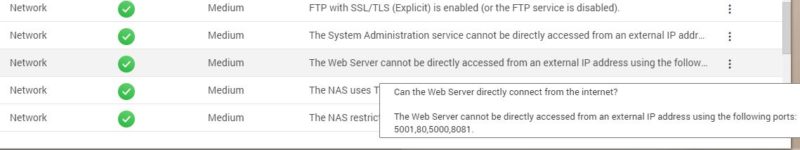
Also, the security advisor can point you to disable UPnP service here:
These are the same two checks that prevent not only this but also the previous attacks from a few weeks ago.
Final Words
While we would agree that QNAP can do more to increase security, at some point, the ecosystem also needs users to take some responsibility. QNAP NASes now have features more akin to traditional servers so we can see why someone may think to just expose them directly to the Internet. Still, victims of these attacks seem to not heed the normal advice of putting the NAS at least behind a firewall/ VPN. There seems to be an education gap between those deploying these NAS units and the basic setup principles. Hopefully, QNAP can help on its end, but for our readers, please get this information out.
If our regular STH readers cannot tell, we recently heard of a small non-profit that fell victim to crypto locking ransomware. We are trying to make a better effort this quarter to make our readers aware, but really we want to have our readers spread the word to raise the level of education on this topic. Anyone with a credit card can buy a QNAP NAS, but we should be helping those that do not deal with IT regularly to know some basics. QNAP also needs to help, but we can do our part as a STH community.




QNAP market their products as safe to attach to the internet. E.g. photo and video sharing services, remote file access and backup etc.
Open question is if it is possible to securely configure a QNAP, and check with their Security Counselor application to permit the internet facing features and services they market and not be hacked?
E.g. is the QNAP cloud access safe / secure functionality?
This article fails to realize that people buy QNAP devices purposely to expose them to the internet. Issue is that those same customers expect default security features to be put in place (ip address lock out after failed access attempts, etc).
I need router ports open to access the device from my phone off premises. Telling me to block access via web is telling
me to not be a customer.
This article is complete nonsense. QNAP come enabled with all of these services out of the box, including direct access.
The whole idea to install an extra program to advise users to disable features enabled by the vendor out of the box is absurd. They SHOULDN’T be enabled in the first place.
So your suggestion that its somehow users fault is absurd. A typical user got this thing at Costco, and will NEVER know what to do. They open a box, plug it in, and forget about it.