Recently QNAP said its NAS units are again under a wave of brute force attacks (see the statement here.) As a result, we are reminding our users to take at least basic steps to protect their NAS units. QNAP ships its NAS units in a relatively insecure manner, and it is up to users to take measures to protect their systems. The company also says the most vulnerable are those directly connecting the NAS units to the Internet, and that is true of most systems. Let us show some examples of basic security steps to take.
Basic Security Steps for Your QNAP NAS
In terms of basic security steps, the first should probably be simply not directly connecting the NAS to the Internet. Most STH readers will use some sort of firewall/ NAT setup, and often a VPN to get to the storage network. One challenge with QNAP NAS units is that they are designed to get updates via repositories on the Internet, meaning they need to have at least some egress access, unlike an IPMI interface. Still, when you get a NAS, it is likely the Security Counselor application will not be installed already.
When you want to install this application, which we recommend, you get asked about sharing results with QNAP.
Still, upon launching the Security Counselor app, you get a short Wizard explaining some of the basic concepts.
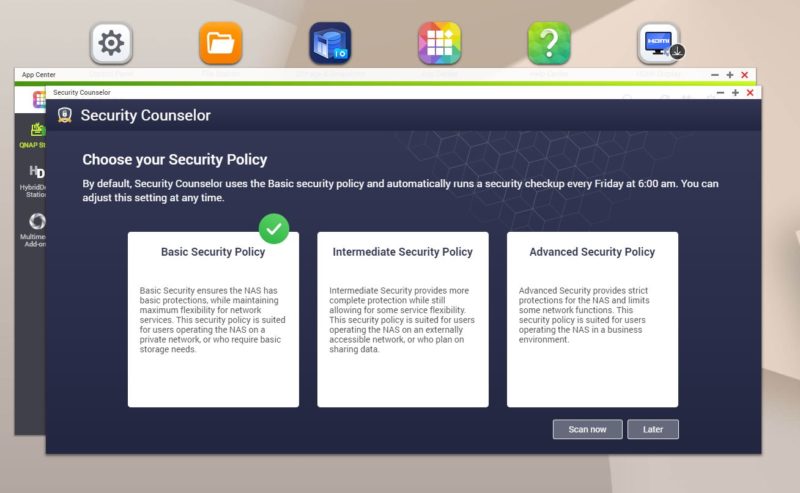
QNAP has some pre-set policies for businesses, SMB, and home users.
The app can automatically adjust settings as required.
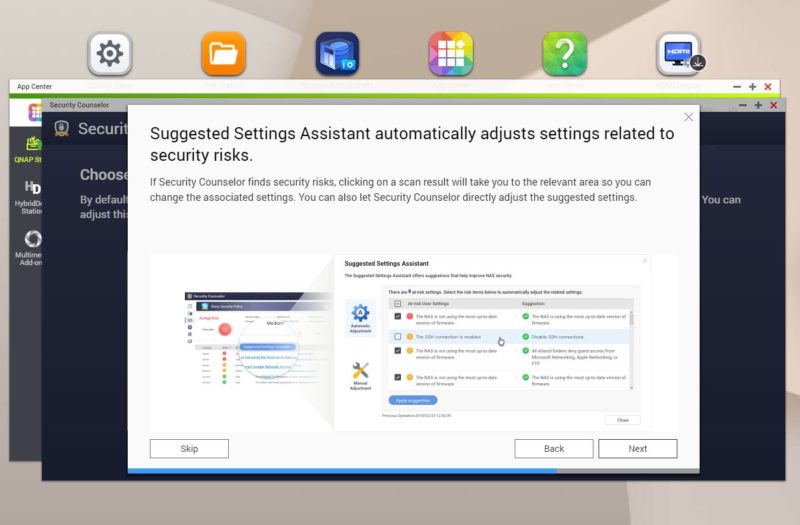
And there is a dashboard that we are going to show shortly.
The first step is picking a policy. While basic is the default, our sense is that STH readers are going to opt for Intermediate or Advanced.
x
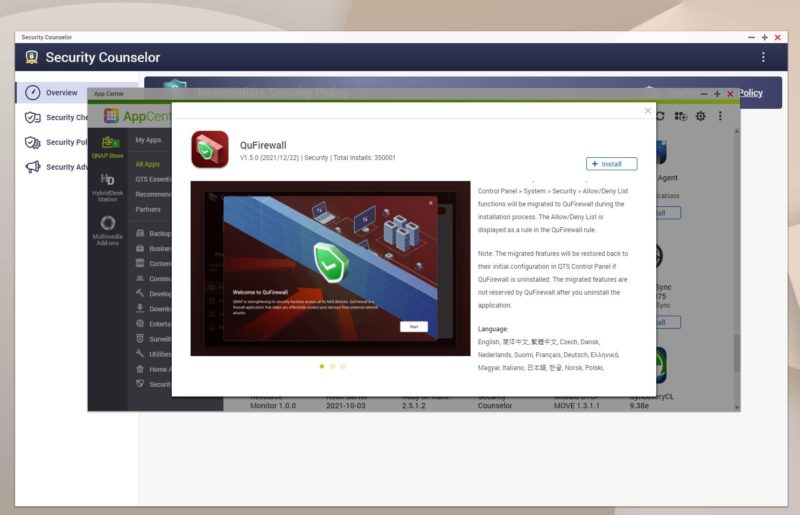
There are a few items that pop up that are important. QNAP does not actually ship its units with a lot of the security features like the antivirus app pre-installed. Instead, one has to install these from the app store. QuFirewall here has not been installed.
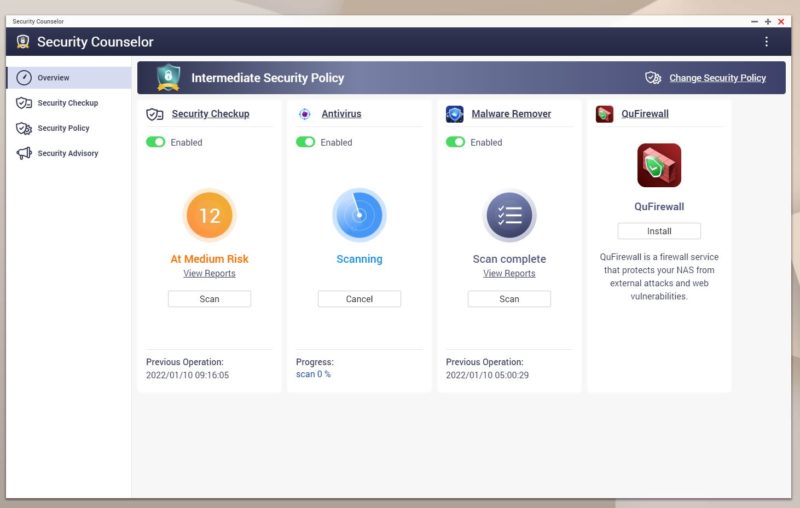
QuFirewall provides basic firewall functionality wrapped in a GUI. Something that seemed strange was that there were only around 350K installs of QuFirewall. Security Counselor has just over 1 million installs in contrast.
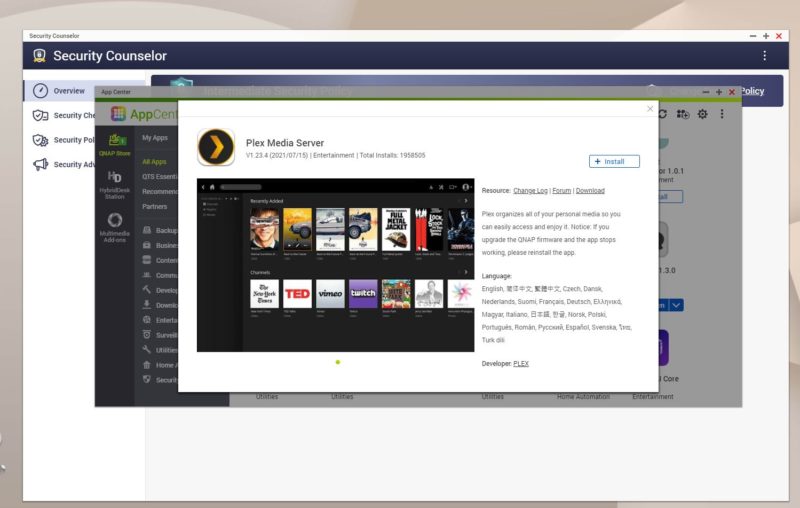
Plex is around 2x the Security Counselor figures at around 1.96M installs.
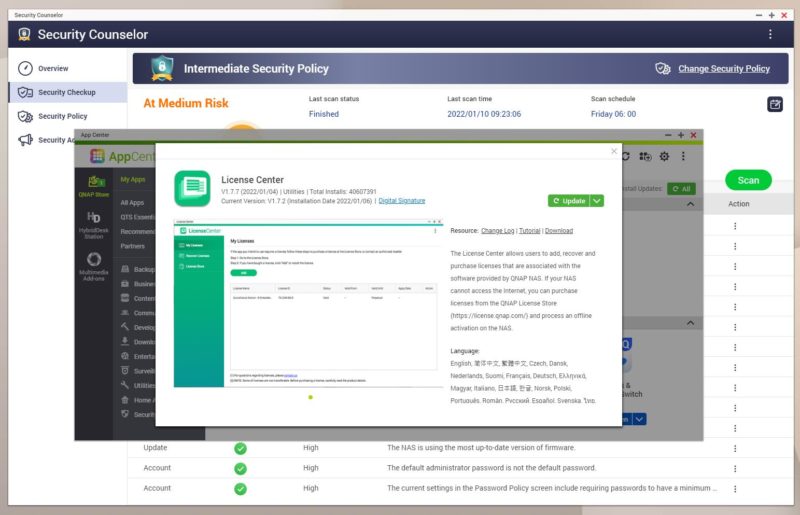
On the funnier side, one of the “medium risk” issues is that License Center is not updated. License Center allows you to manage licenses for the QNAP NAS. This application has over 40M installs. This is a mandatory application, but it seems like the Security Counselor application should not have fewer than 1% of the installs of the License Center. Likewise that the QuFirewall should not be under 3% of the installs.
QuFirewall still has “Basic” but also has more advanced settings.
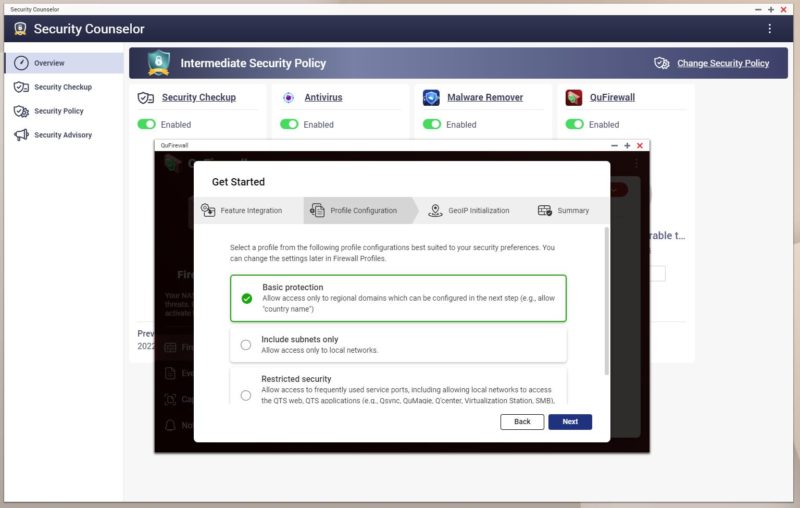
These profiles have built-in rules to allow/ disallow traffic to the NAS based on interfaces, networks, and so forth.
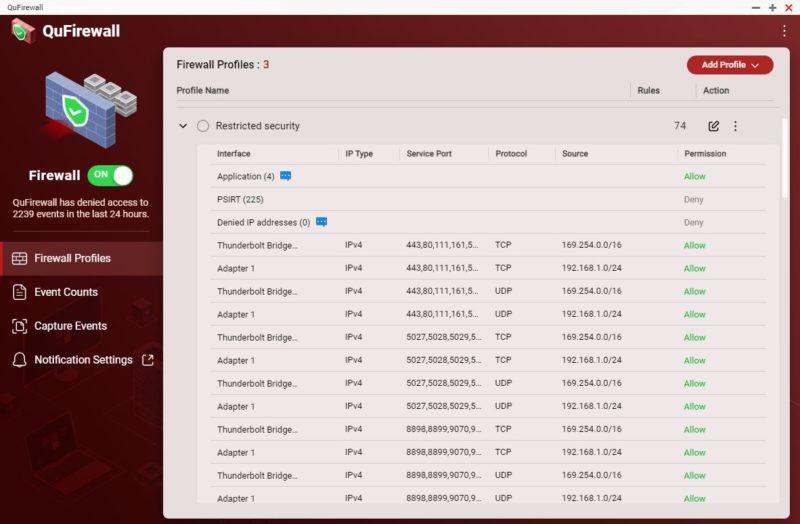
One other important feature is the ability to ban IP addresses for too many failed login attempts.
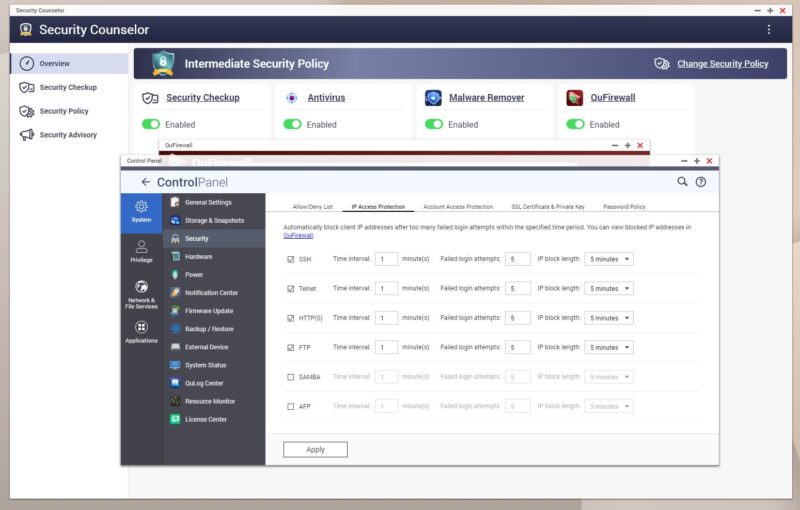
One other item you may want to look at is turning off Telnet (just use SSH) and you can also change the SSH port.
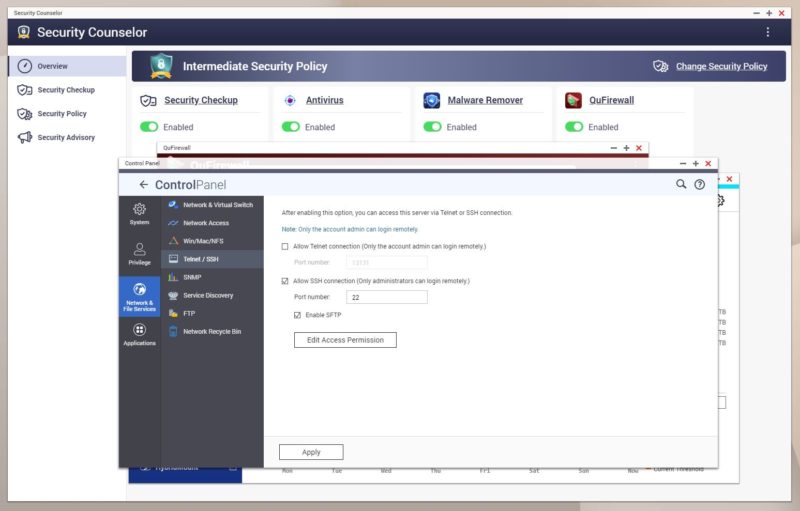
For STH readers, many will want to turn off UPnP since that is commonly exploited.
We also suggest staying up-to-date on firmware and malware removal updates on a QNAP NAS. QNAP is constantly patching for new vulnerabilities so it is important to do.
Final Words
This is one of those pieces that is nowhere near a complete how-to. At the same time, there are some basics that we suggest everyone do. QNAP does as well with the Security Counselor app. At the same time, it seems like there are a lot of NAS users out there not installing firewall features, not running Security Counselor, and so forth.
One area we wish QNAP improved upon is having some kind of baseline security posture for every installation. These units should all have firewalls and it is probably time that Security Counselor becomes standard and part of the initial setup process. Twenty years ago, a small NAS was a cheap box that supported a few protocols to get drives accessible via an Ethernet port. These days, they are becoming full-fledged servers running many services and applications. QNAP already has the tools, we just hope they up the default security setup on their NAS units.
This new security advisory about brute force password attacks on NAS units directly connected to the Internet is a good example of why this needs to change.





It looks like NASes, or at least QNAP, are due for the same reckoning that(to a degree at least) forced vendors to shove the default security settings of consumer desktop OSes from ‘dire’ to ‘more or less sane, though not hardcore paranoid corporate lockdown’.
Shipping things in ‘on your own head be it’ mode is one thing if your firmware is total techhead stuff with a learning curve you can ski down, or fairly strictly for enterprise customers with sophisticated admins or consultants on hand. It’s still not a virtue; but those markets can handle it.
QNAP, though, ships a fairly shiny, friendly, ez-GUI which very much gives the impression that you can bring it online and use it without getting too deep into the weeds: and that’s true if you count only ease of getting it into a state where you can access its features; but dangerously misleading if you(as you should) only count it as ‘working’ if it’s in a reasonably secure state.
Making the product more secure but harder to use is certainly a thankless task; but the alternative is people’s data being vastly less safe than it appears, potential beachheads for lateral movement further in, botnets; and all that delightful stuff.
This article answered the reasons why in the SOHO NASes segment, more and more frequent attacks are happening and will happen. The vast majority of these box owners have believed in marketing in terms of ease of use for home users, even those who have no experience. As a result, prices have fallen, and sales of these devices are skyrocketing. The pandemic only helped to spread such devices across the SOHO segment.
Tens of millions of NASs (we have other vendors here with the same problem) are literally provided with their content for darknet, which needs just an average knowledge to abuse them. I’ve been writing about it for years. The NAS is not a smartphone where a single click is enough, and it’s done. Unless the NAS vendors change the behaviour of the so-called security autopilots and remain in the same behaviour as in the present article, then nothing will change.
The problem is much more complex. Because these users have believed that a cheap modem/router from an ISP is a regular choice for home internet. The vast majority of such network appliances are below average in terms of security, and again, the average educated hacker can break them if you name them that.
So here’s the behaviour:
– cheap data boxes
– cheap network appliances
and regular reports of data misuse in the hundreds of thousands a year from this segment.
This civilization will die out “cheaply” or “free” once.
On the other hand, we have users of such boxes who prefer to buy a new overpriced laptop, desktop computer or mobile phone. Best once a year. To be in. But I will refuse to give even 300 Euros to network and data security. This is not to be liked on social networks. And no one understands that.
So the only thing you can think of vendor and others is to recommend – disconnect your devices from the Internet. Great advice.
And there is another fire – I can start writing about the topic of using docker containers with copy/paste settings from dubious sources that spread these bad habits. After all, it’s great to have a free “server” at home that works with my data.
I didn’t know that security counselor existed. You’re right it should be part of the standard setup process.
I can’t believe they just let you connect this to the open Internet without a firewall. Then people wonder why they’ve gotten a bad reputation for security.
I’m wondering what sorts of ISPs people have that they can connect a device directly to the internet with a public IP. I do get a public IPv6 prefix but even the Router provided by the ISP filters out any traffic unless explicitly allowed.
Businesses with working at home employees need to pick the best product with the best security. Not all businesses have NAS or any know how.
Security is a selling point.
My Qnap Nas was attacked by translate recently. I have tried to scan the nas using malware remover but it gave me an error message. I have no idea what to do next.
The QNAP NAS here is pretty well segmented from anything of importance on one side and the dangers of the Internet on the other. Even so, I decided to update the firmware because of this security problem. The immediate result was more than half the computers mounting iSCSI network block devices served by the QNAP no longer do so.
I’ve been looking at error logs, web searches and more error logs since Thursday night. Even through none of the user-land tools on the NAS are standard and everything runs with root permissions, I wouldn’t complain if it worked.
Unless something changes, my plan tomorrow is to mount the targets on one of the machines that mysteriously still connects to the QNAP and migrate the data to something standard, less fashionable and a lot more power hungry–a standard Xeon server with a bunch of disks.
It’s been an astonishing waste of time, and that’s just the update with no malware involved.
Here is a quick followup to my previous post. Downgrading to QTS 4.5.x from the newly installed 5.0.x series fixed the problem with the iSCSI targets. Fortunately, there was also an updated image for 4.5.x on the download page so hopefully the recent round of security blunders are solved in that version as well. I wonder what to do when the next round of updates come out.
How do I get this Security Counselor app? It doesn’t exist in the app center.