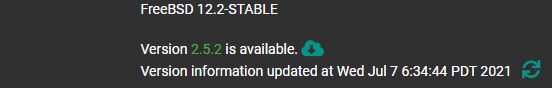
The newest pfSense Community Edition release is now out. This version is dubbed the pfSense CE 2.5.2 release. This is a minor release but it is bringing back Wireguard support as an experimental add-on. For those who missed this, CE is effectively the “free” pfSense edition when pfSense 2.5 was released with more bifurcation between the CE and Plus variants.
pfSense CE 2.5.2 Released
This is a dot release, but it is important. There are a few new features in the new version, and one we want to make our readers aware of. The key items Netgate highlighted are:
- WireGuard can now be installed as an experimental add-on package
- Additional hardware support
- Fixes for AES-NI encryption
There were also a large number of dynamic DNS updates. These include new support for:
The solution already supports a number of dynamic DNS providers, but this is good to see since it provides more options for folks.
Since we have a bit of experience with this after the FreeNAS Corral fiasco, and we had users request that we do this, we wanted to see what would happen to users who deployed pfSense 2.5 with Wireguard and who were stuck using the first implementation. For those that missed it, pfSense and FreeBSD pulled back on kernel WireGuard support. Still, that took some time so we wanted to take a look at what the experience is if you saw the kernel support, deployed Wireguard, and then got stuck with an unsupported Wireguard solution when support re-emerged.
For those that want to deep dive into the updates, you can find the release notes here.
pfSense CE 2.5 to pfSense 2.5.2 Wireguard Upgrade
We have a test node setup with pfSense 2.5.0 with kernel Wireguard since we wanted to see what would happen when support came back.
When one goes through the upgrade process, here is what they see:
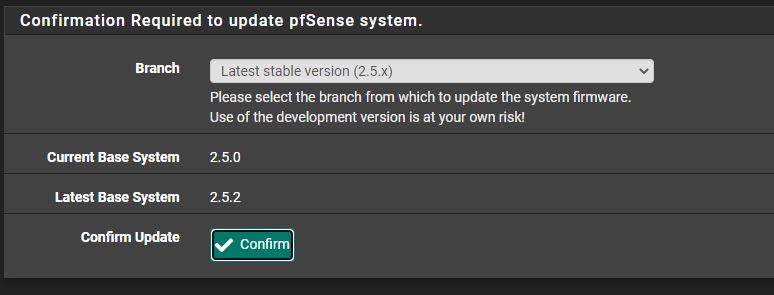
The upgrade ultimately fails. Please note this was the same as we saw in pfSense 2.5.1 so this behavior is completely expected.
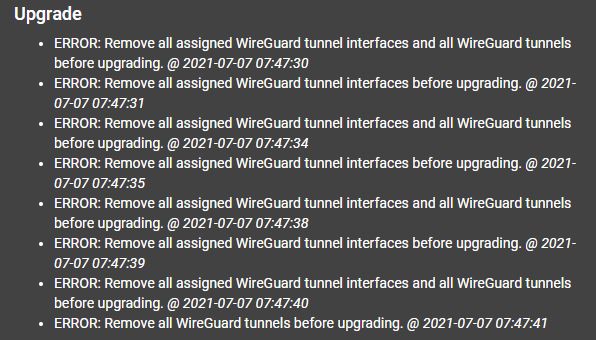
For those early kernel Wireguard adopters that are stuck, the configuration is not imported into the experimental add-on in the new version. There are a number of reasons that this makes sense since it would involve an upgrade plus add-on step and is only relevant for a smaller number of users as a one-time task.
Our best advice given what we are seeing is to not hope for an easy upgrade path. Instead, it is probably worth setting up OpenVPN, using that connection to remotely do upgrades, then re-enabling Wireguard through the OpenVPN tunnel. That somewhat defeats the purposes, but it is likely what will need to be done. We wanted to do this quick test over a period of time just to see what the outcome would likely be and it seems like we have an answer.




Thanks for specifically testing out the upgrade with Wireguard. I too am stuck on 2.5.0. I don’t have too many tunnels to re-create but at least I know there is a path forward now.
This is why I switched to OPNSense… pfSense while great once, has just gone downhill very fast.
pfSense is still working fine for me. I haven’t needed to switch to anything else.
There are a number of issues with OPNSense too, so as usual it’s a case of the grass not really being greener on the other side of the fence. :-)
Not running WireGuard here, but went tried to upgrade our pfSense box yesterday and it bricked the box. Old box was running 2.4.5-p1. There was a console, but that’s it. I couldn’t get it to pass traffic, webconfigurator wouldn’t come up, OpenVPN wouldn’t respond inside or outside.
Fortunately some kind souls out there have older pfSense images available for download SINCE PFSENSE REFUSES TO HOST OLD VERSIONS…GRRRR, so I was able to wipe it and restore our backup file. I will say that wiping/restoring from USB worked nice enough, but still…
ALWAYS make backups before you update anything.
pfSense is dead to me. When I finally took a look at the “OPNsense.COM” site they created which portrayed the OPNsense team as Nazis and “retards”, I was disgusted.
What I discovered was a plush and vibrant ecosystem with OPNsense. Far more modules can be added. There is also a simplicity that cuts through unneeded complications. Am I 100% happy? Not yet, but it’s growth has been astonishing compared to pfSense which has largely stagnated. If one last module were to defect to OPNsense, it would be a no brainer for everyone.
If you haven’t seen the .COM (.CON ?) site, it is on the WayBackMachine. The complete lack of ethical, moral and business Sense that went into that site is staggering.
@Alex, unfortunately a backup without the old version of pfffftSense is a difficult restore at best. Good idea to keep old versions and get new ones on your own when updating through the GUI.
I failed to mention ^^ that STH didn’t give a complete and unbiased account of the Wireguard fiasco: the complete lack of business (and even ethical) Sense in that case was again staggering. The pfSense management team is questionable at best.
Can we get an update on supported NICs for pfsense especially the 25gbe? Also can we get a simple benchmark page that shows routing performance with different classes of CPU’s?